39 defense in depth diagram
Surface drives security through a defense in-depth approach by utilizing a layering of independent defensive sub-components. From chip to cloud, or a UEFI that ensures a Root of Trust to the AI powered Microsoft Defender for Endpoint that works to prevent, detect, investigate, and respond to advanced threats, Surface enforces the position that ... The low-water line is derived from the coastal State's own charts. 1. These zones are measured using nautical miles, a measurement based on the circumference of the Earth. 2 One nautical mile equals roughly 1.15 miles on land. As seen in the graphic below, the LOSC divides the ocean into six different zones: 1.
This is completely the opposite of VAT. The whole point of VAT is that it isn't double taxation -- if a business buys wholesale for $80 and sells retail for $100, they only have to collect VAT on the $20 difference and not the whole $100, because the wholesale seller already collected it on the $80.

Defense in depth diagram
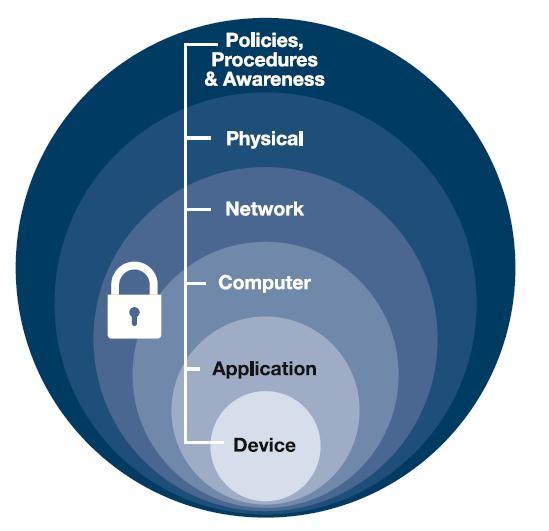
Defense in Depth (DiD) refers to an information security approach in which a series of security mechanisms and controls are thoughtfully layered throughout ... The Department of Defense is America's largest government agency. With our military tracing its roots back to pre-Revolutionary times, the department has grown and evolved with our nation. The "Defense in Depth" concept now provides optimum protection against various threats and risks in the form of a phased defense strategy. Play it safe, too! A reliable water supply for the Ruhr area
Defense in depth diagram. The newsroom in Cleveland is expected to hire 25 staffers to launch by mid-2022. The donors said it will produce "original, in-depth, non-partisan reporting" that will be free to access ... Moreover, they help our security teams learn about the engineering process in depth, building relationships between engineering teams working together during ICS cyber incidents. ICS security managers can start a consequence-driven tabletop with guidance outlined in the blog entitled Top 5 ICS Incident Response Tabletops and How to Run Them . May 13, 2020 — If you were to look up defense in depth on the internet, you'd find a lot of information along with diagrams, images, documentation, ... Defense in depth is a concept used in Information security in which multiple layers of security controls (defense) are placed throughout an information ...
The U.S. Department of Defense, General Motors, Google, the CERT Coordination Center and over 1,300 other organizations have partnered with HackerOne to find over 120,000 vulnerabilities and award over $80M in bug bounties. HackerOne is headquartered in San Francisco with offices in London, New York, the Netherlands, and Singapore. How the Buccaneers protect duo, their bread-and-butter run play. By Ted Nguyen Nov 30, 2021 8. The Buccaneers offense lives and dies on the arm of Tom Brady and its talented receiving corps but ... The US Infrastructure Bill has significant implications for technology Learn where IT funds will be allocated under the congressionally passed Infrastructure bill.; Adoption and Change Management is your key to digital transformation In six minutes, we cover the importance of ACM and how it supports technology usage and employee satisfaction.; Cutting edge announcements from day one of ... The building up, layering on, and overlapping of security measures is called "defense in depth." [157] In contrast to a metal chain, which is famously only as strong as its weakest link, the defense in depth strategy aims at a structure where, should one defensive measure fail, other measures will continue to provide protection.
The goal of the DoD Cybersecurity Policy Chart is to capture the tremendous breadth of applicable policies, some of which many cybersecurity professionals may not even be aware of, in a helpful organizational scheme. The use of colors, fonts, and hyperlinks is designed to provide additional assistance to cybersecurity professionals navigating their way through policy […] The NES, Accessories, and The Legend of Zelda. The NES was a best-selling console, producing games from 1985 to 1995. The first releases were Donkey Kong, Donkey Kong Jr., and Popeye. The NES was also revolutionary for including multiple accessories with the console, enhancing the already new and appealing gameplay. The Ravens have activated running back Nate McCrary and defensive back Robert Jackson from the practice squad ahead of Sunday's game against the Pittsburgh Steelers. McCrary is a COVID-19 ... Defense-in-depth is an information assurance strategy that provides multiple, redundant defensive measures in case a security control fails or a vulnerability ...
Defense in Depth (DiD) is an approach to cybersecurity in which a series of defensive mechanisms are layered in order to protect valuable data and ...
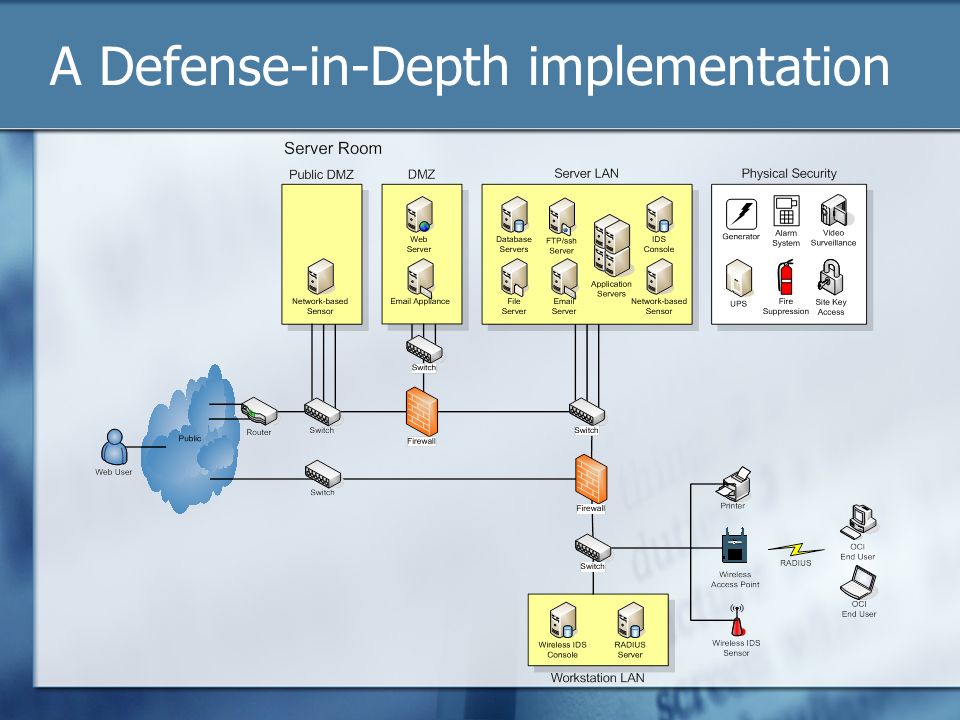
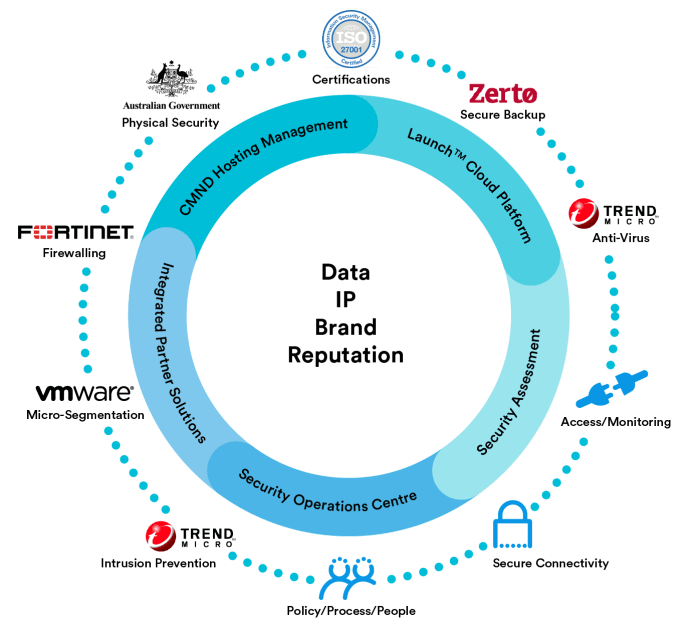
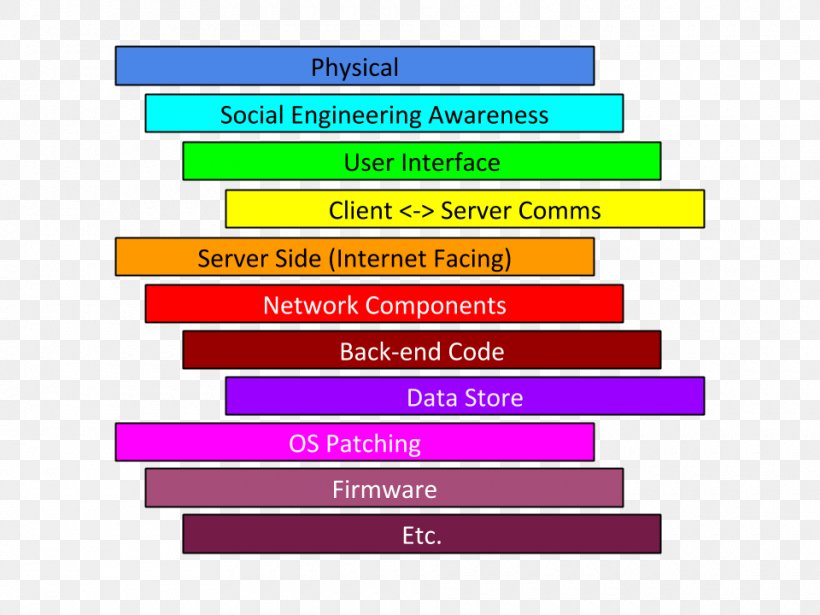
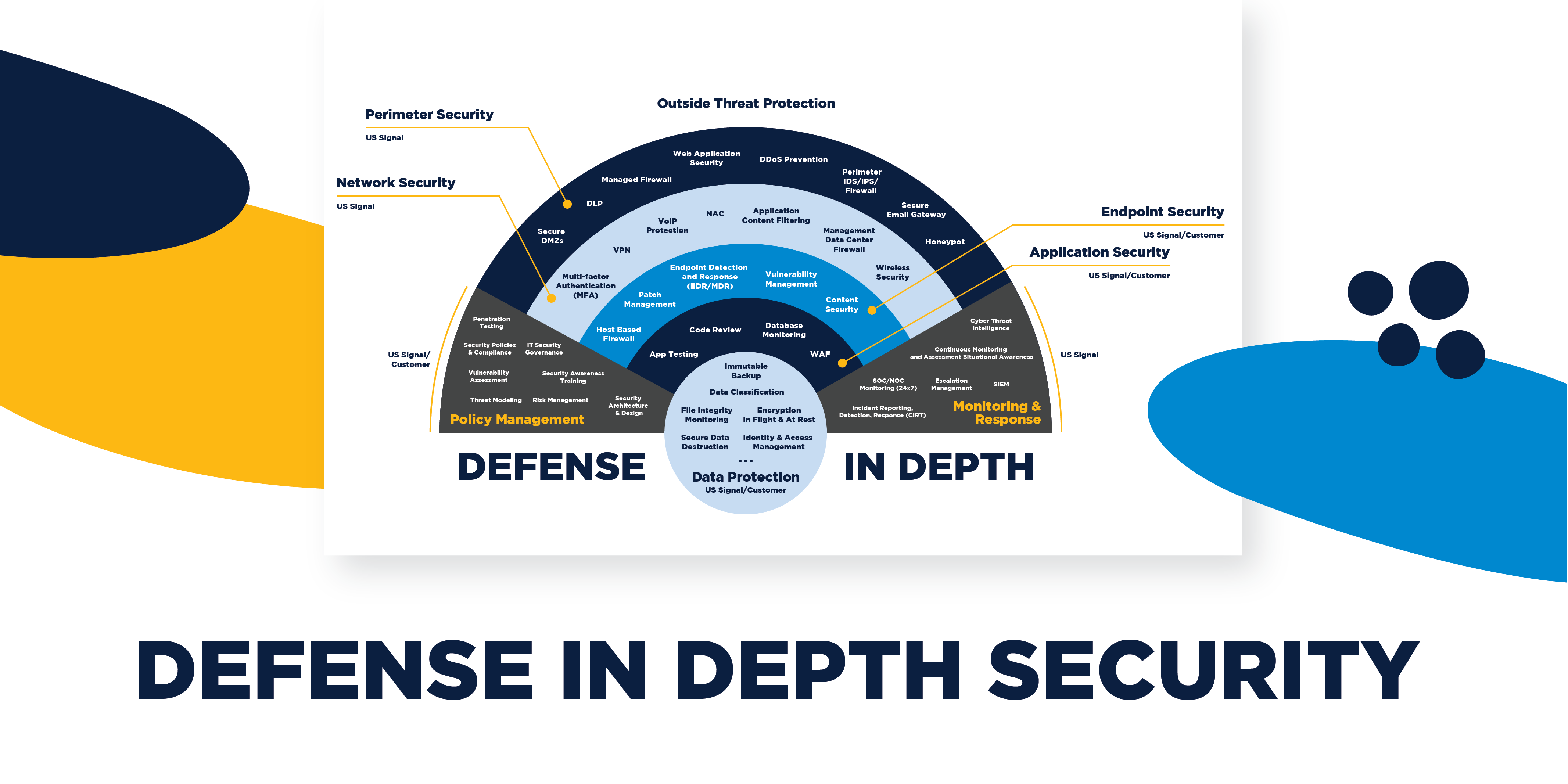
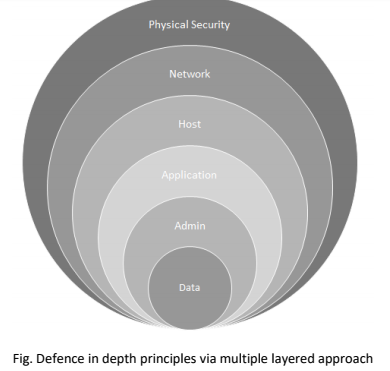
Below is a network diagram showing the architecture of the IT and OT environments and where to best deploy security controls to ensure a defense-in-depth protection strategy. By applying security controls and policies in all layers of the network architecture, the organization will make it more difficult for attacks to succeed.
The report provides a study with an in-depth overview, describing the Product/Industry Scope and elaborates market outlook and status (2021-2031). ... and collateral diagrams depicting a different ...
Feb 2, 2021 — Defense in depth is a holistic approach to cybersecurity. The concept revolves around placing multiple layers of security protocols to protect ...
Analysis. What Ourlads' Scouting Services said about MAC JONES before he made the New England Patriots' Depth Chart: Alabama, 6025 217 4.83. Redshirt junior entry, one-year starter, Jacksonville, FL. Also started four games the year prior when Tua Tagovailoa went down with a season ending hip injury.
Cybersecurity, data diodes, Defense in Depth, demilitarized zones (DMZ), ... The diagram shown in Figure 5 depicts an integrated architecture that includes ...58 pages
Investigation shows how Facebook and Google fund misinformation globally by paying millions of dollars in ad revenue to the operators of clickbait pages — A month after the fall of the democratic government.— In 2015, six of the 10 websites in Myanmar getting the most engagement …
Proper network security controls can provide defense-in-depth elements that. Defense-in-Depth IATF Release 3.1 September 2002 08/02 UNCLASSIFIED 2-1 Chapter 2 Defense in Depth 2.1 Introduction and Context Diagrams Defense in Depth is a practical strategy for achieving information assurance (IA) in today's highly networked environments.
Nation Nov 17, 2021 12:03 PM EST. MADISON, Wis. (AP) — Kyle Rittenhouse shot three men, killing two of them and wounding the third, during a protest against police brutality in Kenosha ...
The report provides a study with an in-depth overview, describing the Product/Industry Scope and elaborates market outlook and status (2021-2031). ... and collateral diagrams depicting a different ...
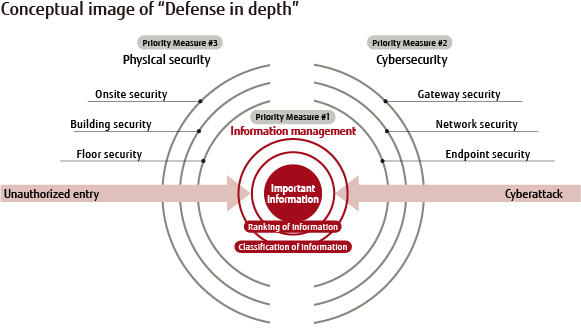
Download scientific diagram | Layers of defense in depth architecture. from publication: Cyber Defense In Depth: Designing Cyber Security Agency ...
04 Low Maintenance and Attention. Machine-learning is applied to create dynamic deception campaigns that simplify ongoing deception environment authenticity, refresh, and redeploy after a compromise is detected. Engagement-based alerts prevent false-positives, automate attack analysis and incident response actions, and remove operation burden.
This diagram looks at a delay game tactic. This strategy and spacing are hard to disrupt. The concept is very simple - use a down screen out of a 2-1-2 alignment to milk the clock, looking for opportunities to attack if the defense extends too far. The embedded video below has plenty of clips to see the strategy in action.
The 870 Express has a rather thick back end, which keeps it from slipping out of position. This will help reduce the risk of a sore shoulder, which can really ruin your hunt. The extra thickness also helps minimize recoil, and bird hunters often find it ideally shaped for the task.
The integrated solution from CySight and Keysight eliminates blind spots offering unprecedented network visibility and defense in depth. 2021.10.11 Solution Briefs 2021.09.29
Defense-in-depth exploits mitigations. To further mitigate the risk of a security compromise, Microsoft has invested in numerous defense-in-depth mitigations in Azure systems software, hardware, and firmware to provide strong real-world isolation guarantees to Azure customers.
If anything, the above scenario is a good example of why a defense-in-depth strategy is required. And even though Microsoft Defender for Endpoint has anti-tamper protection capabilities, it doesn't prevent from (locally) updating firewall rules.
Head Coach: Brian Kelly. Offensive Schemes: Spread. Defensive Schemes: Multiple 3-3-5. Updated: 11/22/2021 3:48PM ET. COLOR LEGEND FOR DEPTH CHARTS---PURPLE-Top Rated UNDERCLASSMEN- EARLY ROUNDS-GREEN: 1/2 ROUNDS,RED: 3/4 ROUNDS- AQUA: 5/6 ROUNDS, BLACK: 7/PRIORITY FREE AGENT, GRAY- FA/CAMP . GOLD- New additions Graduate transfers & freshmen. Pos.
The history of the Internet has its origin in the efforts to build and interconnect computer networks that arose from research and development in the United States and involved international collaboration, particularly with researchers in the United Kingdom and France.. Computer science was an emerging discipline in the late 1950s that began to consider time-sharing between computer users, and ...
The "Defense in Depth" concept now provides optimum protection against various threats and risks in the form of a phased defense strategy. Play it safe, too! A reliable water supply for the Ruhr area
The Department of Defense is America's largest government agency. With our military tracing its roots back to pre-Revolutionary times, the department has grown and evolved with our nation.
Defense in Depth (DiD) refers to an information security approach in which a series of security mechanisms and controls are thoughtfully layered throughout ...





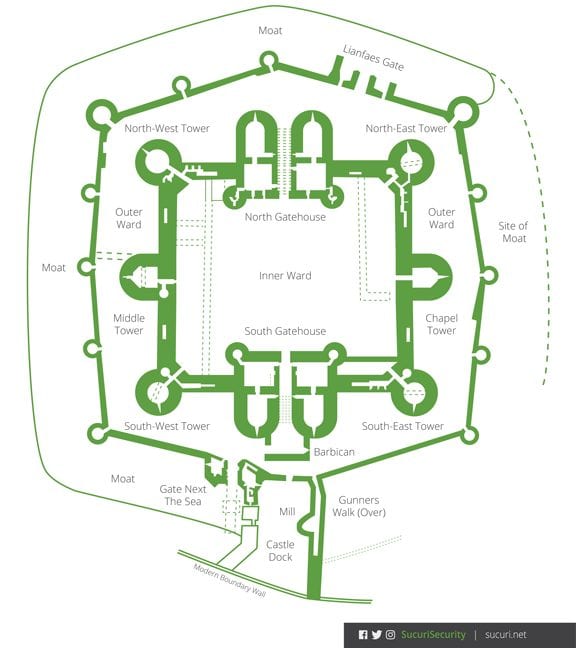
















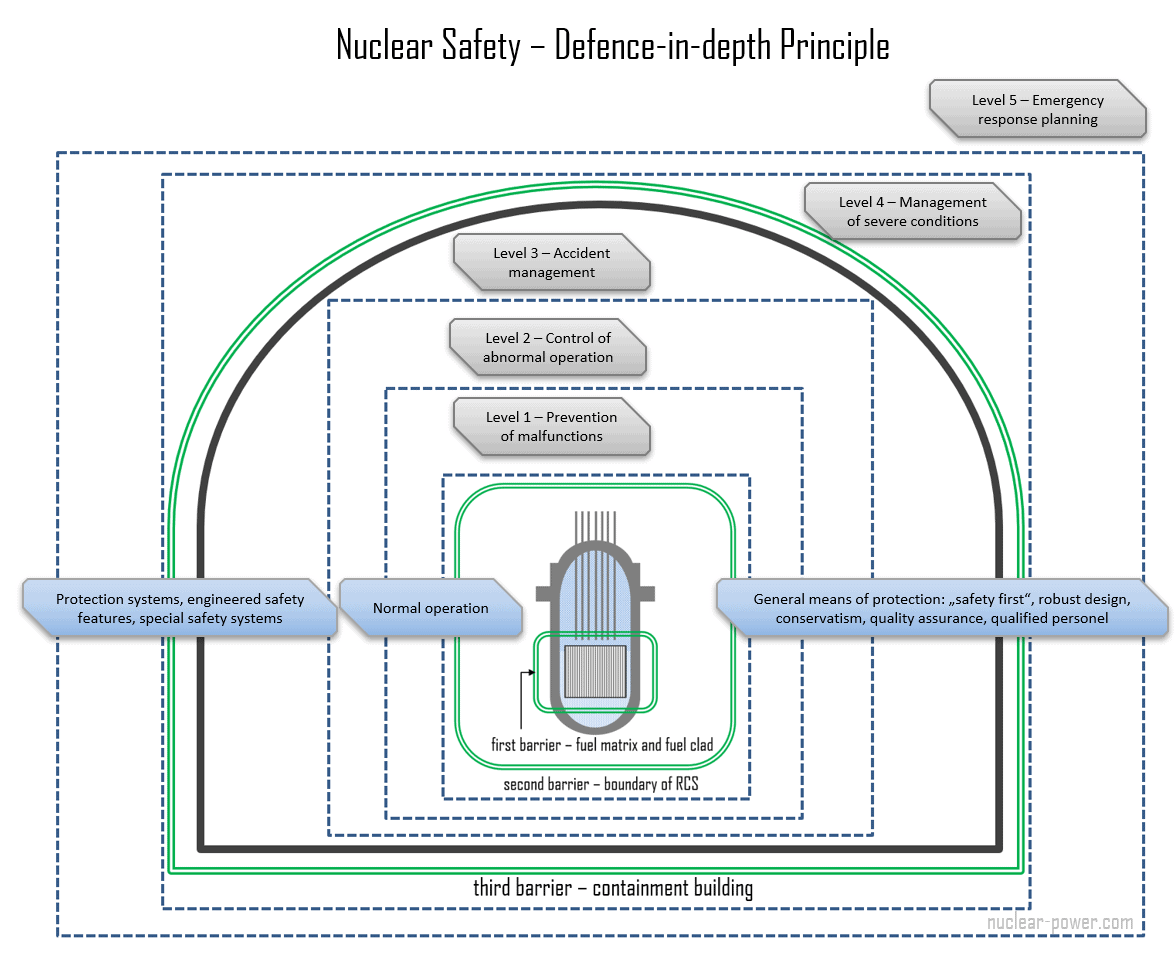
0 Response to "39 defense in depth diagram"
Post a Comment